Introduction
The Samsung Knox Cloud Services (KCS) team is pleased to introduce a new Role-Based Access Control (RBAC) capability that allows customer (tenant) admins who are responsible for account creation (Super Admin) to assign more refined role permissions to individual admins as their specific enterprise requirements dictate. Though each supported Knox Cloud Service, Knox Configure (KC), Knox Mobile Enrollment (KME), Knox Guard (KG), and the Reseller Portal (RP) utilizes admin roles unique to that service, a Super Admin cuts across all services.
With the new RBAC service, existing customers will have their administrators migrated automatically with the next Knox Cloud Service release in Q1 2019. Administrators with their own unique set of permissions (manage administrators, delete devices etc.) will be assigned new roles that map to their current permissions. If needed, new roles beyond what the migrated admins are currently assigned can be created based on a list of permissions unique for each service.
Keep in mind, the only role that cannot be assigned is the Super Admin role, which applies across all supported services. Only one person can assume a Super Admin role per company. Upon migration, the Super Admin role is assigned to the person who originally created the customer account. The Super Admin role receives every permission available.
Migrate existing admins to Role-Based Access Control (RBAC)
Each service has different permissions available to its administrators. Every combination of service permissions is mapped to a different role. The role names are generic by default, but can be modified based on your organization’s naming requirements.
For example, a KME admin with the ability to invite other admins will be mapped to “KME Role 1”. Or a KC Admin with the ability to both (i) delete and (ii) unassign profiles from devices will be mapped to “KC Role 2”. Impacted KCS Admin Guides will be updated with the details of these mappings when RBAC is released later in Q1.
However, for KG and its large number of permission combinations, there is no mapping table. The easiest way to ascertain which permission the role has, is to click on the role name in the Roles table.
Create a role and assign permissions
Each Knox Cloud Service has different permissions that can be combined and assigned a role. The following role creation example is from the Knox Mobile Enrollment console.
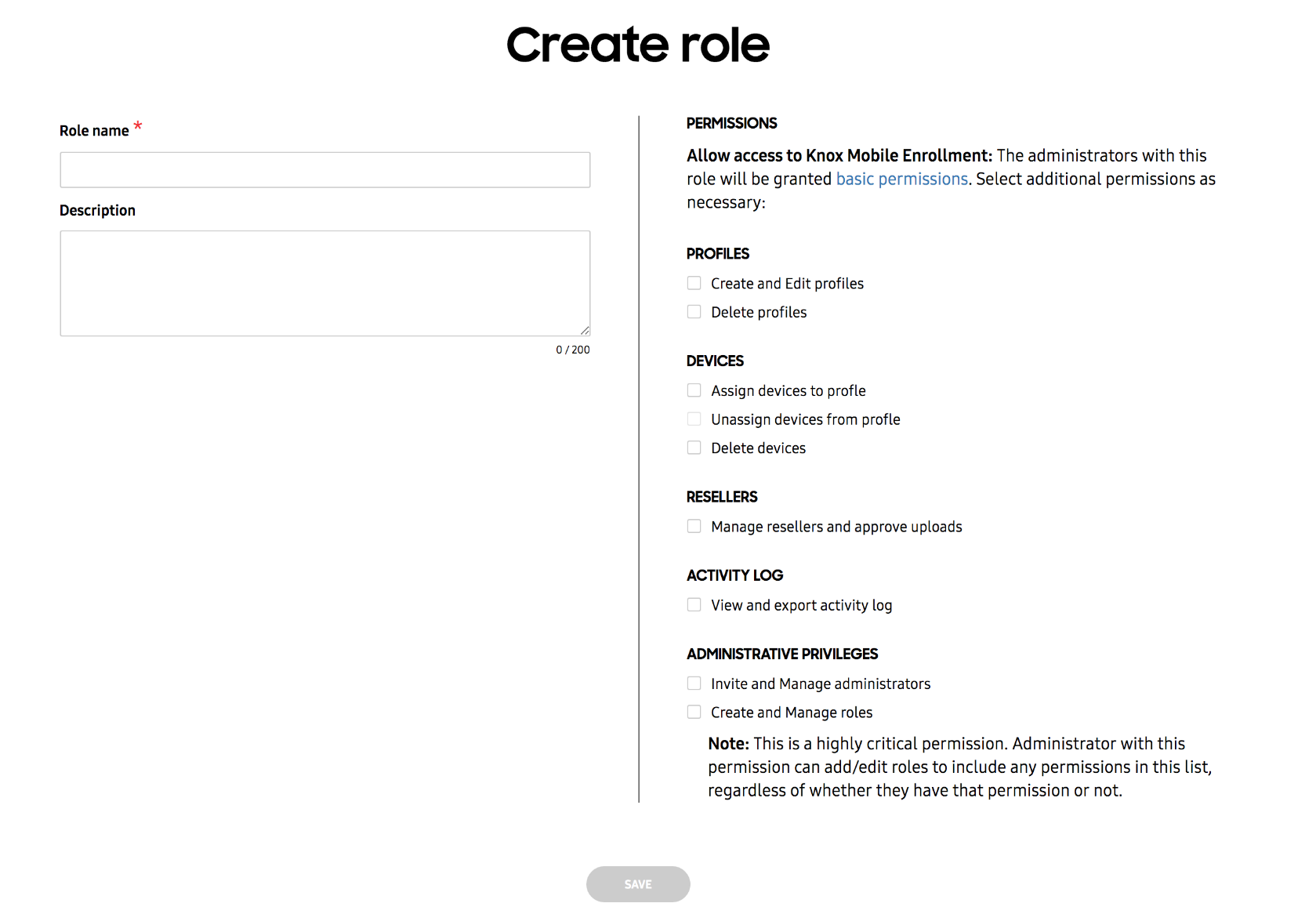
Once the required Role name is defined, specific permissions can be selected by category as needed for the particular role. New administrator roles receive some basic permissions by default, but additional permissions require assignment for individual roles. Keep in mind, a role must be first created before an administrator can be invited to that role.
The console navigation and screens required for role and administrator invitation vary slightly amongst impacted services.
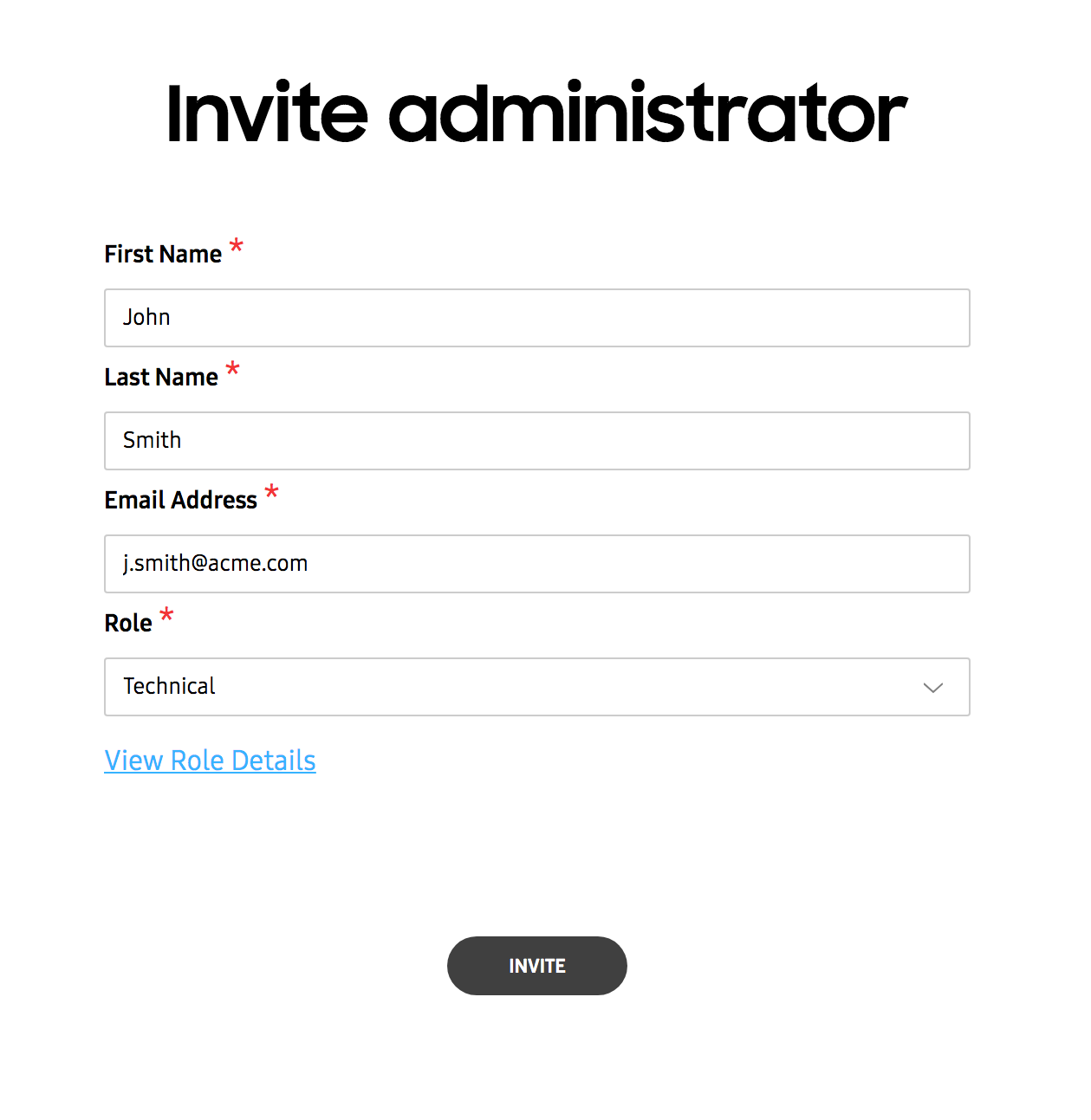
Invite a user to be an administrator with a defined role
Existing users require an invitation to become an administrator. However, as noted previously, a role must first be created that can be assigned to the administrator. Provide the name and Email address serving as the administrator’s contact resource, then select the Role assignment for this specific administrator.
Viewing Roles
Once roles have been created and assigned to administrators, they can be reviewed to assess whether the role name requires modification or its permissions need refinement.
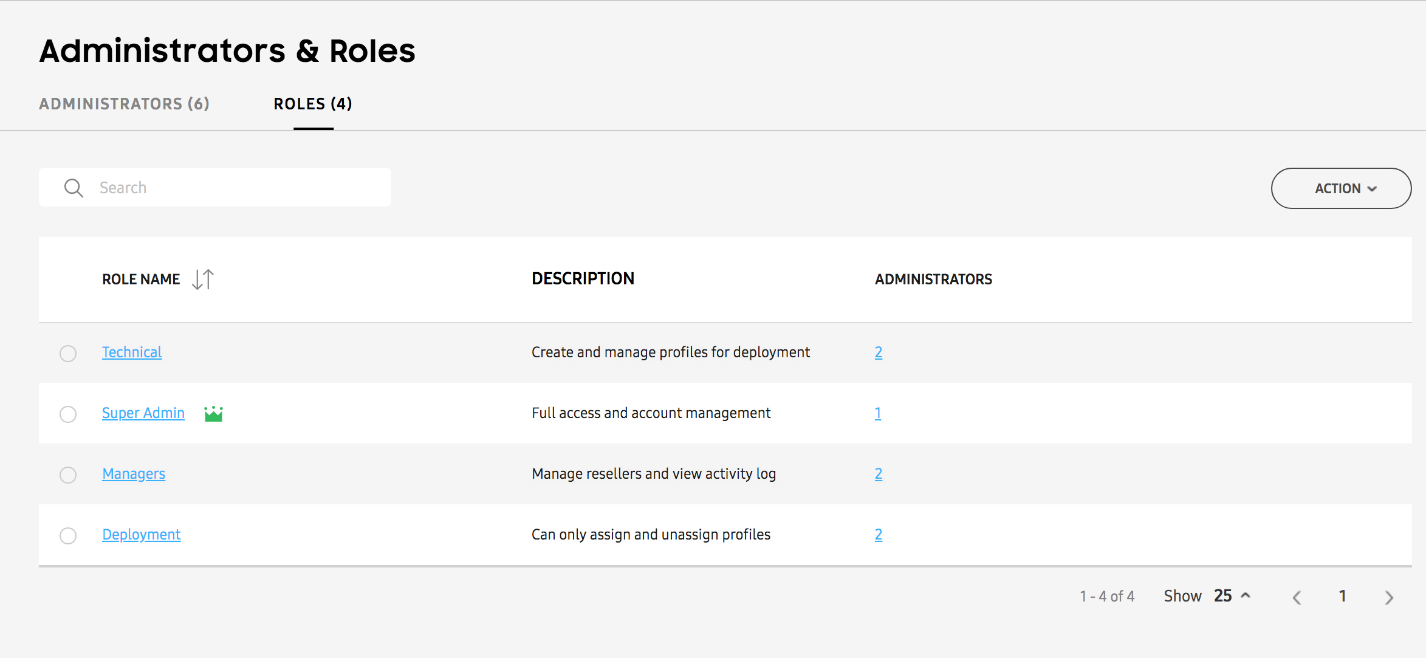
More than one administrator can be assigned the same role. The number of administrators assigned a particular role displays as a link that can selected to view the names of the assigned administrators.
User interface customization for particular roles
Each KCS console will be customized for each role, depending on the permissions granted. For example, an Admin without Administration Privileges will not display “Administrators & Roles” in the left-hand navigation menu.
What’s next
Over time, the KCS team will be expanding the permissions available to a Super Admin. The updates will be communicated in a timely manner.